VA continues to integrate with the business, manage information risks more strategically, and work toward a culture of shared cyber risk ownership across the enterprise.
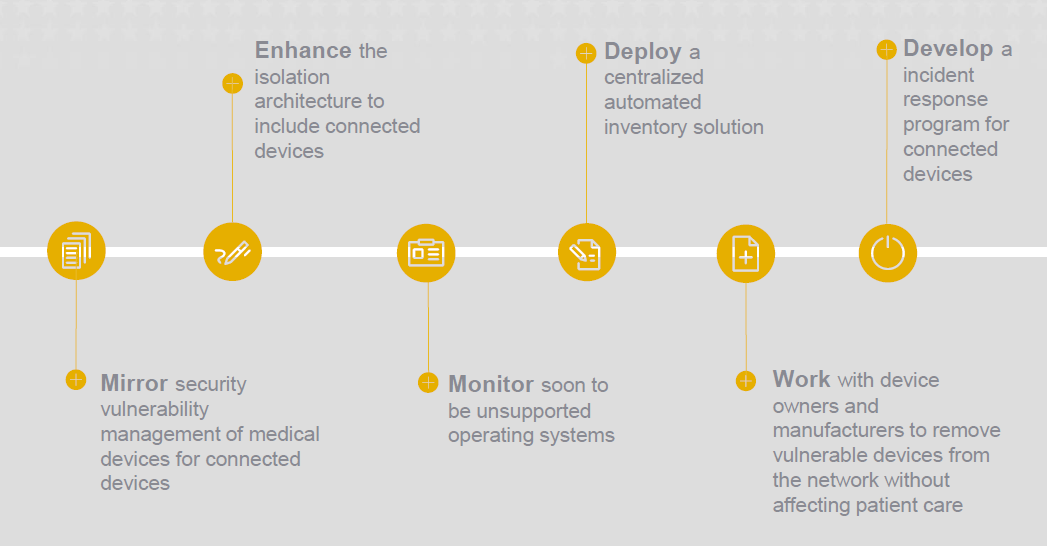
• Mirror security vulnerability management of medical devices for connected devices
• Enhance the isolation architecture to include connected devices
• Monitor soon to be unsupported operating systems
• Deploy a centralized automated inventory solution
• Work with device owners and manufacturers to remove vulnerable devices from the network without affecting patient care
• Develop an incident response program for connected devices