Project Description
In March 2012, the VA consolidated information security initiatives into the Continuous Readiness in Information Security Program (CRISP) to increase security for information that VA holds about individual Veterans, especially health care records and the Internet of Things (IoT). A hallmark of CRISP is that all VA employees have a direct, personal responsibility to safeguard the privacy of sensitive information about Veterans. This responsibility extends to VA contractors, volunteers at VA facilities, representatives of major Veterans service organizations, trainees and others who deal with Veterans’ information at VA.
As part of the CRISP team assembled by Accenture Federal Services, KRM staff members were instrumental in the creation of the inventory tool, translating client detail from documentation to database/front end and subsequently refining the processes for ensuring data quality, facilitating data intake, and refining the types of data collected. The effort involved consulting with the client stakeholders to create architecture for the SPS Inventory tool and develop the intake process and identify the data points to collect. Ongoing collaboration resulted in improvements to the data inventory tool and methods for ensuring the quality of data, filtering raw data and making determinations, based on requirements, of what should be included or excluded in the inventory tool (SPS identification) while generating analytics and reports on the data collected. In the ongoing maintenance of the process and tool, KRM engineers are working with stakeholders as a liaison for quality control of data collected for the inventory tool, and to maintain quality of the tool over it’s lifetime, improving any of the aspects above, mostly data quality and data categorization.
The Threat Landscape
The purpose for developing this inventory tool is to ensure that the system administrators will have, at their fingertips, the ability to identify and locate any devices in use that may be vulnerable to the more sophisticated methods for penetrating networks and devices in use by hackers today. While the hackers make detection and prevention of cyber attacks more difficult, CRISP provides an avenue for getting ahead of them by identifying and cataloging the potential targets, allowing remediation to take place prophylactically.
The Veterans Health Administration (VHA) is the largest integrated healthcare system in the United States providing care at 1233 Health Care Facilities, 168 VA Medical Centers, and 1052 Outpatient sites serving more than 8.9 million Veterans each year. The VA environment spans six data centers with over 1,800 locally-managed facilities and 750,000 network devices. With this complex environment, applying cybersecurity consistently is difficult and requires collaboration across several disciplines to protect the data of our Veterans. Some factors affecting VA’s threat landscape:
- Explosive growth and use of information technology devices connected to the Internet – “Internet of Things” (IoT), some examples of IoT at VA:
- Networked Medical Devices – used in patient health care for diagnosis, treatment, or monitoring of physiological measurements, or for health analytical purposes*
- Special Purpose Systems (SPS) – network-connected, non-medical systems that play a critical role in supporting a VA facility’s operations and mission fulfillment (e.g., heating, ventilation, and air conditioning (HVAC); water control)*
- Proliferation of information systems and networks with virtually unlimited connectivity via mobile technologies and the cloud lending to a larger attack surface:
- 750K protected devices on the VA network
- 5M emails monitored per day, 75% blocked due to malware and other malicious activity
- Increasing sophistication of threats including exponential growth rate in ransomware and distributed denial of service (DDoS) attacks leveraging the IoT vulnerabilities. The opportunity for a malicious attack or a security breach continues to increase as more devices are becoming Internet-enabled.
VA’s Approach to Improving Security
The VA Enterprise Cybersecurity Strategy Team (ECST) within the Office of Information Technology (OI&T) was established to mature VA’s cybersecurity posture and safeguard Veteran information that is essential to providing quality health care, benefits, and services to our nation’s Veterans. The ECST works to secure VA’s medical devices, special purpose systems and other IoT devices.
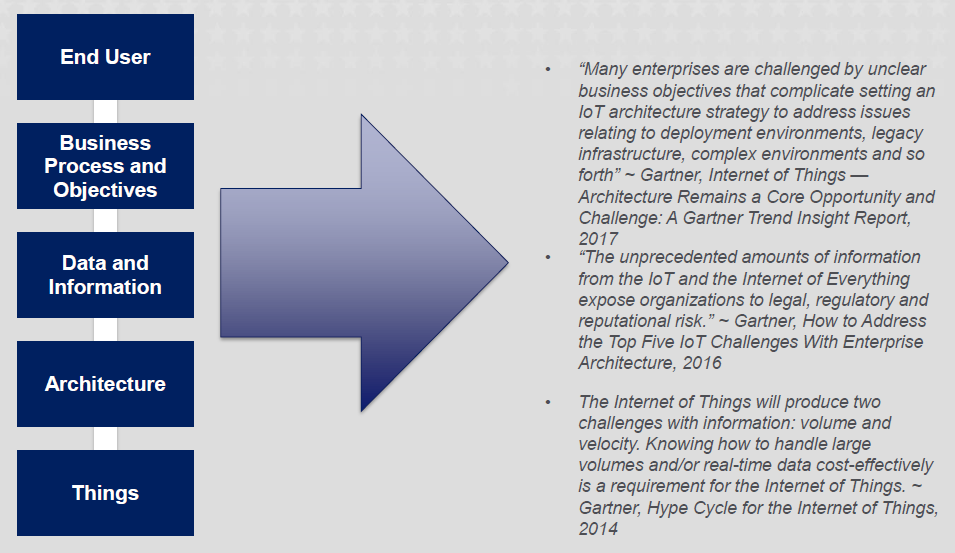
Source: http://www.himssconference.org/sites/himssconference/files/pdf/188_0.pdf
They take advantage of recent enhancements in technology to find new ways to collect, analyze, share, and act on the data to drive operational efficiencies in support of their mission. The increasing emphasis on securing these devices prompted the Department of Homeland Security (DHS) to issue six strategic principles to securing IoT:
- Incorporate Security at the Design Phase
- Promote Security Updates and Vulnerability Management
- Build on Recognized Security Practices
- Prioritize Security Measures According to Potential Impact
- Promote Transparency Across IoT Connect Carefully and Deliberately
Examples of VA Addressing the Security Challenges of IoT
The roadmap for enhances security requires scaling solutions enterprise-wide and establishing protections for connected devices on the VA network, covering end users, business processes and objectives, information, data, architecture and things.
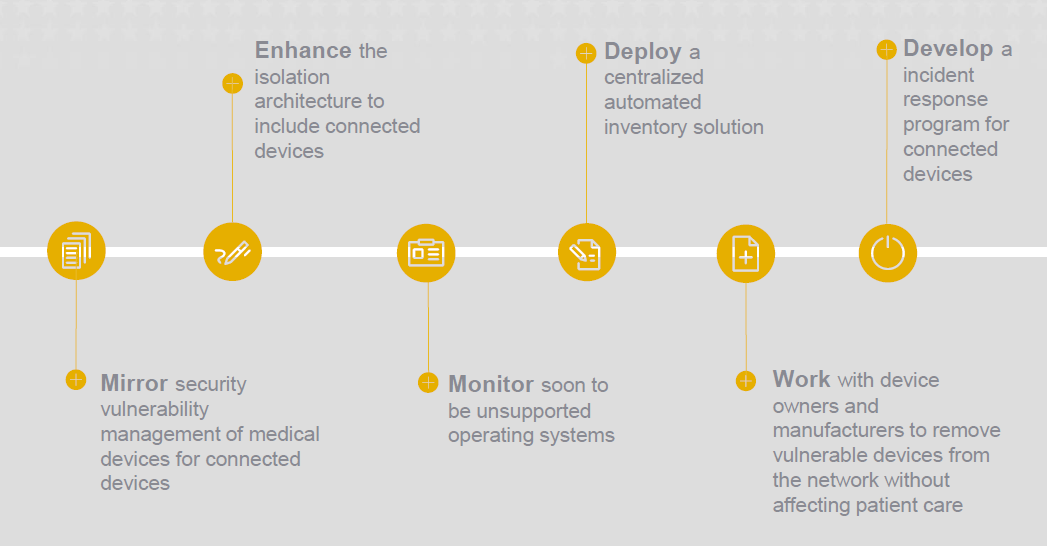
Source: Source: http://www.himssconference.org/sites/himssconference/files/pdf/188_0.pdf
Some of the solutions in place and in work covering major challenges are shown below:
- Vulnerability Management
- Deployed of VA’s Medical Device Vulnerability Management Program.
- Created the security control overlay for medical devices
- Published and integrated a cyber incident root cause analysis into standard operating procedures (SOP)
- Aging Infrastructure
- Implementation of the Isolation Architecture Change Advisory Board to evaluate and recommend improvements to standardized processes and procedures established to control VA IT infrastructure changes
- Asset Management
- Implemented an automated inventory tool and an inventory reconciliation process
- Unsupported Operating System
- Leveraged an isolation architecture for medical devices connected to their network.
- Implemented a change management advisory board
- Governance and Risk Management Solutions
- Deployed a Medical Device Protection Program
- Provided security, guidance, training and outreach to VA employees and contractors
- Implemented continuous monitoring of evolving cybersecurity threats
- Implemented configuration controls
- Implemented incident response to remediate security breaches
Evolution of VA’s Approach to Securing IoT
KRM’s work with VA continues to integrate with the business, manage information risks more strategically, and work toward a culture of shared cyber risk ownership across the enterprise.
- Mirror security vulnerability management of medical devices for connected devices
- Enhance the isolation architecture to include connected devices
- Monitor soon to be unsupported operating systems
- Deploy a centralized automated inventory solution
- Work with device owners and manufacturers to remove vulnerable devices from the network without affecting patient care
- Develop an incident response program for connected devices